Difference between revisions of "NetMan - pfSense"
| (17 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
| + | <span style="background-color: rgb(153, 204, 0); color: rgb(0, 0, 255);" data-mce-style="background-color: #99cc00; color: #0000ff;">'''<big>Now on Wiki.NerdMage.Ca</big>'''</span> | ||
| + | |||
=Download pfSense= | =Download pfSense= | ||
[https://www.pfsense.org/ Where to get it] | [https://www.pfsense.org/ Where to get it] | ||
| Line 4: | Line 6: | ||
[[File:Screenshot from 2020-06-08 14-31-42.png|256px|Screenshot from 2020-06-08 14-31-42.png|alt="Aaarrrggg!"|right]] | [[File:Screenshot from 2020-06-08 14-31-42.png|256px|Screenshot from 2020-06-08 14-31-42.png|alt="Aaarrrggg!"|right]] | ||
| − | <br /> | + | See that nifty screencap over there on the right? |
| + | |||
| + | Look at it again. | ||
| + | |||
| + | '''<big>It's important...<br /></big>''' | ||
==Stuff it onto a thumbdrive== | ==Stuff it onto a thumbdrive== | ||
| Line 89: | Line 95: | ||
[[pfSense - Menu Structure|Menu Structure]] | [[pfSense - Menu Structure|Menu Structure]] | ||
| + | |||
| + | ===All the fancy stuff=== | ||
| + | (Coming soon<sup>TM</sup>... Promise<sup>TM</sup>...) | ||
| + | |||
| + | *[[NetMan - Dynamic DNS|Configuring Dynamic DNS]] | ||
| + | *[[PfSense - Managing DHCP|Managing DHCP]] | ||
| + | *[[PfSense - Managing NAT on the firewall|Managing NAT on the firewall]] | ||
| + | *[[PfSense - Multi-Wan Configuration|Multi-Wan Configuration]] | ||
| + | *[[PfSense - Private VPN|Private VPN]] | ||
| + | *[[PfSense - Crap-Stopping with pfBlockerNG|Crap-Stopping with pfBlockerNG]] | ||
| + | *[[PfSense - Etc...|etc...]] | ||
=Troubleshooting & Repair= | =Troubleshooting & Repair= | ||
| Line 109: | Line 126: | ||
<code>arp -d -a</code> | <code>arp -d -a</code> | ||
| + | |||
| + | =Port Forwarding= | ||
| + | |||
| + | *[https://www.netgate.com/docs/pfsense/nat/forwarding-ports-with-pfsense.html Forwarding Ports with pfSense] | ||
| + | *[https://forum.netgate.com/topic/50236/port-forwarding-step-by-step-demystified-pfsense-2-solved Port Forwarding - Step-by-Step - Demystified - pfSense 2 [SOLVED]] | ||
| + | *[https://www.yougetsignal.com/tools/open-ports/ Open Port Check Tool] | ||
| + | *[https://community.spiceworks.com/topic/1978690-what-am-i-missing-on-setting-this-port-forward-for-rdp-on-pfsense What am I missing on setting this port forward for RDP on pfSense?] | ||
| + | |||
| + | ==Connecting to the VPN machine through the firewall== | ||
| + | |||
| + | *'''SEARCH:''' [https://www.google.com/search?q=bind+vnc+to+network+interface bind vnc to network interface] | ||
=Notes & Tips= | =Notes & Tips= | ||
| − | + | ==If you want to be able to ping your network from the outside, Go into Firewall / Rules / WAN & create a rule to allow ICMP.== | |
| + | [[File:PfSense-ICMP-rule.png|left|thumb]] | ||
| + | <div style="clear: both"></div> | ||
| + | |||
| + | ==To adjust the size of your subnet on the internal LAN connections:== | ||
| + | |||
| + | *Select '''Interfaces / LANx''' | ||
| + | *Under '''Static IPv4 Configuration''', change the [https://techterms.com/definition/subnet_mask subnet mask][[File:PfSense - Subnet Mask.png|frameless]] (probably from the default '''/24''') | ||
| + | **Just a note, pfSense uses [https://docs.netgate.com/pfsense/en/latest/book/network/understanding-cidr-subnet-mask-notation.html CIDR Subnet Mask Notation] | ||
| + | |||
| + | Here's a handy [https://www.freecodecamp.org/news/subnet-cheat-sheet-24-subnet-mask-30-26-27-29-and-other-ip-address-cidr-network-references/ Subnet Cheat Sheet] | ||
| + | |||
| + | =Some Links= | ||
| − | + | *Some rather good tutorials at [https://blog.monstermuffin.org/ Muffin's Lab]: | |
| + | **[https://blog.monstermuffin.org/pfsense-guide-nat-firewall-rules-networking-101/ pfSense: A Guide to NAT, Firewall Rules and some Networking 101] | ||
| + | **[https://blog.monstermuffin.org/tunneling-specific-traffic-over-a-vpn-with-pfsense/ Tunneling Specific Traffic over a VPN with pfSense] | ||
| + | **[https://blog.monstermuffin.org/create-an-ipsec-site-to-site-tunnel-between-two-pfsense-firewalls/ Create an IPSEC Site to Site tunnel between two PfSense firewalls] | ||
*[https://doc.pfsense.org/index.php/Installing_pfSense Installing pfSense] | *[https://doc.pfsense.org/index.php/Installing_pfSense Installing pfSense] | ||
*[https://www.youtube.com/watch?v=ledv33t6SNE Build a Router 2016 Q4 - pfSense Build] | *[https://www.youtube.com/watch?v=ledv33t6SNE Build a Router 2016 Q4 - pfSense Build] | ||
*[https://www.youtube.com/watch?v=8jYibgeAV0Y Whole-network VPN with pfSense Router] | *[https://www.youtube.com/watch?v=8jYibgeAV0Y Whole-network VPN with pfSense Router] | ||
*[https://www.youtube.com/watch?v=bkWJ8Cmn03I pfSense: How to Setup in DataCenter on VM-ware ESXi (Morton Hjorth)] | *[https://www.youtube.com/watch?v=bkWJ8Cmn03I pfSense: How to Setup in DataCenter on VM-ware ESXi (Morton Hjorth)] | ||
Latest revision as of 18:09, 27 December 2021
Now on Wiki.NerdMage.Ca
Contents
Download pfSense
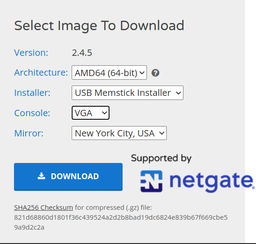
See that nifty screencap over there on the right?
Look at it again.
It's important...
Stuff it onto a thumbdrive
(really should create command-line instructions for this part)
If working from a Linux Mint machine GUI, right-click & extract the .gz file. Then right-click the resulting .img file & select "Make bootable USB stick".
If working from one of those crappy Windows machines, use Rufus...
If you're playing with a Mac... Yer on yer own for now.
Configure the Hardware
You'll want either a dual NIC or 2 (or more...) NICs.
A hard drive (or SSD) could come in rather handy...
Install pfSense
- Boot your machine from the thumbdrive. (UEFI is just fine...)
- Accept the copyright.
- Select "Install"
- Select "Continue with default keymap" (or, really, any keymap you like...)
- Select "Auto (UFS)
- Choose your disk for the install
- I'd suggest only having one disk in the machine...
- Select "Entire Disk
- Yes... Proceed.
- Select GPT (GUID Partition Table)
- Hit "Finish"
- Hit "Commit"
- Watch the pretty progress screens... (Or ignore it until it's done... Your choice...)
- When you see the "Manual Configuration" screen, Hit "No"
- Hit "Reboot"
- Go back & configure the machine to actually boot from the drive you installed pfSense onto...
Initial Configuration of pfSense
On first boot, pfSense will ask "Should VLANs be set up now [y|n]?"
Don't bother...
- Select your WAN interface
- bce0 on this test machine (T310)
- Select your LAN interface
- bce1 on this test machine (T310)
- Verify they're selected properly & say yes.
- Watch all the "done" messages scroll by (or not... again, your choice...)
After a moment or 3, you'll see the console menu.
*** Welcome to pfSense 2.4.5-RELEASE (amd64) on pfSense *** WAN (wan) -> bce0 -> v4/DHCP4: 192.168.0.26/24 LAN (lan) -> bce1 -> v4: 192.168.1.1/24 0) Logout (SSH only) 9) pfTop 1) Assign Interfaces 10) Filter Logs 2) Set interface(s) IP address 11) Restart webConfigurator 3) Reset webConfigurator password 12) PHP shell + pfSense tools 4) Reset to factory defaults 13) Update from console 5) Reboot system 14) Enable Secure Shell (sshd) 6) Halt system 15) Restore recent configuration 7) Ping Host 16) Restart PHP-FPM 8) Shell Enter an option:
It's ALIVE!!!
Configuring pfSense from here...
At this point, you should be able to connect to the LAN port & point a web browser at 192.168.1.1
This is the Web-UI...
Default login is:
- Username: admin
- Password: pfsense
Change this. Do it NOW!
If you have the WAN port connected to the Internet, you should actually be capable of accessing the outside world right now.
All the fancy stuff
(Coming soonTM... PromiseTM...)
- Configuring Dynamic DNS
- Managing DHCP
- Managing NAT on the firewall
- Multi-Wan Configuration
- Private VPN
- Crap-Stopping with pfBlockerNG
- etc...
Troubleshooting & Repair
Clearing the DNS Forwarder Cache
To clear the DNS Forwarder cache, restart the dnsmasq daemon as follows:
Click Status / Services
Find dnsmasq in the list
Click ![]() , or stop the service using
, or stop the service using ![]() then start again with
then start again with ![]() .
.
Restarting the daemon will clear the internal cache, but the client PCs may still have cached entries.
Flushing the ARP Cache
Click Diagnostics / Command Prompt
arp -d -a
Port Forwarding
- Forwarding Ports with pfSense
- Port Forwarding - Step-by-Step - Demystified - pfSense 2 [SOLVED]
- Open Port Check Tool
- What am I missing on setting this port forward for RDP on pfSense?
Connecting to the VPN machine through the firewall
- SEARCH: bind vnc to network interface
Notes & Tips
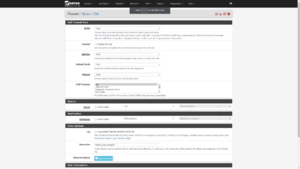
If you want to be able to ping your network from the outside, Go into Firewall / Rules / WAN & create a rule to allow ICMP.
To adjust the size of your subnet on the internal LAN connections:
- Select Interfaces / LANx
- Under Static IPv4 Configuration, change the subnet mask
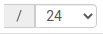 (probably from the default /24)
(probably from the default /24)
- Just a note, pfSense uses CIDR Subnet Mask Notation
Here's a handy Subnet Cheat Sheet